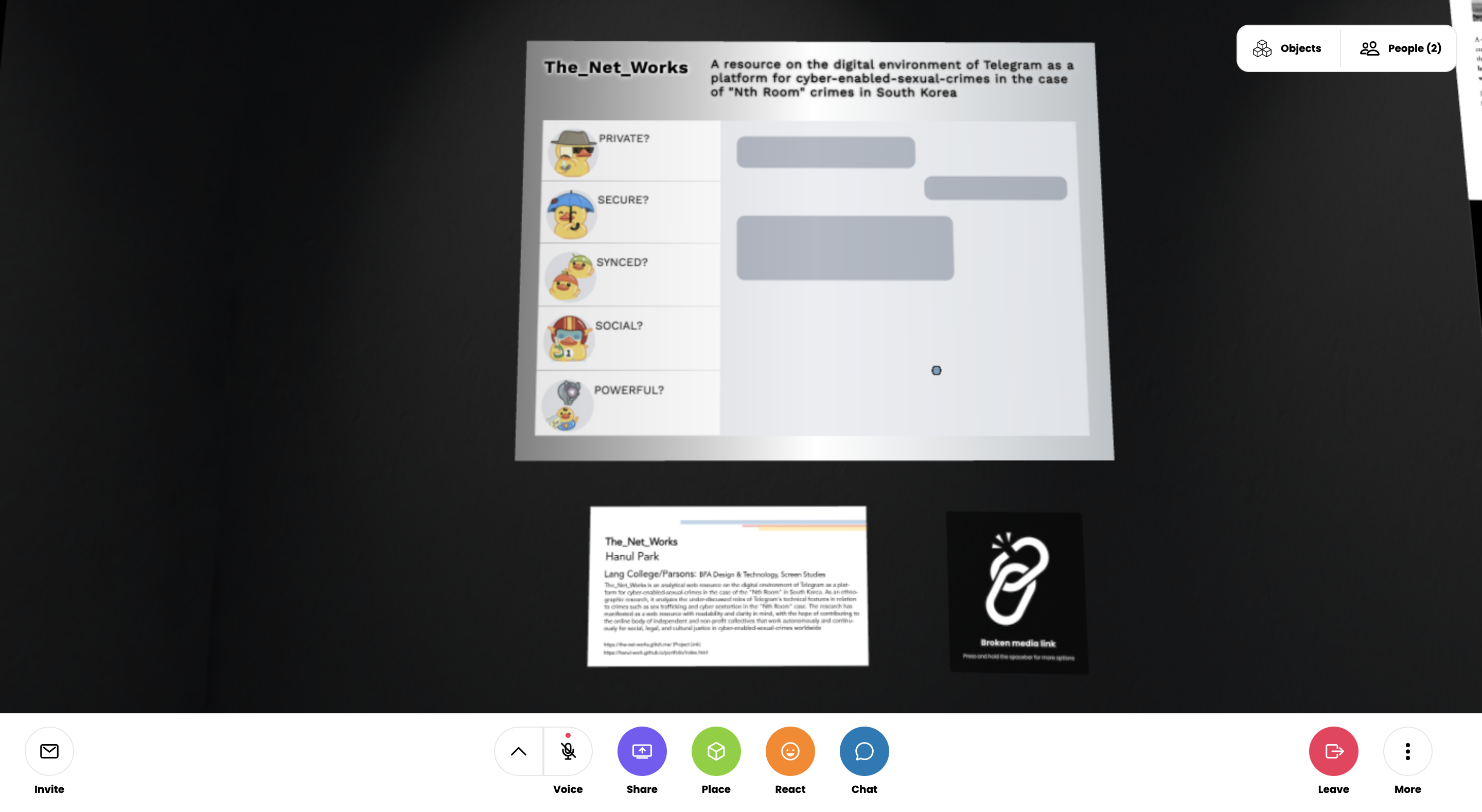
The_Net_Works
Ethnographic Analysis + Web Design + Front-End Development
A Resource on the Digital Environment of Telegram as a Platform for Sexual Cyber-Enabled-Crimes in the Case of "Nth Room" Crimes in South Korea, created in
Glitch
2021
Tool | Google Data Studio, Sheets, Figma
Code | HTML, CSS, JavaScript
Anthropology & Design Exhibition VR Space
PUBLISHED SITE
I. CONCEPT
WHAT
This research project delves into the cyber environment of the messaging platform Telegram, specifically analyzing its role in the infamous "Nth Room" case, a harrowing example of sextortion and human trafficking. The project sheds light on the often-overlooked aspects of Telegram's technical features that may have facilitated these crimes. Employing an ethnographic approach, the research is visualized as an interactive web map resource. This contribution aims to serve as a valuable tool for online communities and collectives working towards global justice in the fight against digital sex crimes.
WHY
This project investigates the role of Telegram, a secure and widely used messaging platform, in facilitating the horrific "Nth Room" case. This case involved a series of interconnected digital sex crimes, including blackmail, sextortion, and the distribution of exploitative content. While the crimes themselves have garnered significant attention, the technical aspects of Telegram that may have enabled them remain under-scrutinized.
This research addresses this gap by employing an ethnographic approach to analyze Telegram's cyber environment. By examining the "Nth Room" case through this lens, the project aims to illuminate how specific features of the platform may have contributed to the crimes' scope, duration, and complexity. The resulting web map resource, "The Net Works," serves as a critical exploration of this connection, offering valuable insights for online safety advocates and policymakers working to combat digital sex crimes.
HOW
This project employs an ethnographic approach to investigate the Telegram environment in the context of the "Nth Room" case. Ethnography involves immersing oneself in a particular social setting to understand its culture and practices. In this case, the research will analyze user behavior, platform functionalities, and the broader online discourse surrounding the case.
By examining how Telegram's features (e.g., encryption, anonymity) potentially interacted with the abusive culture within the platform, the project aims to illuminate the factors that may have contributed to the crimes' severity and scale. This analysis will be visualized through an interactive web map resource, "The Net Works," which will map these interconnections and serve as a tool for online safety advocates and policymakers.
The project's findings are expected to contribute to a more nuanced understanding of the complex relationship between technology and social harm. It seeks to move beyond simplistic narratives of "democratic technology" by highlighting the potential for misuse within seemingly neutral tools. Ultimately, this research aims to spark critical conversations about privacy, anonymity, and the ethical responsibilities of technology companies in creating safer online spaces.
II. ANNOTATED BIBLIOGRAPHY
Kim, Hyejin. Current Status of Response to Digital Child Sexual Slavery and Comparative Analysis of Overseas Crime Prediction System Using Artificial Intelligence. Journal of Digital Convergence, vol. 18. no. 7, 2020, pp. 357-368.
This article, authored by the CEO of the Global Digital Sexual Crime Policy Research Institute, offers a critical analysis of the "Nth Room" case. The author delves into the criminal methods employed, highlighting how the perpetrators exploited Telegram's secure communication features and darkcoin exchange systems. The article emphasizes the devastating mental and psychological impact on the victims, prompting a necessary discussion about the role of technology in facilitating new forms of sexual exploitation.
Several key findings resonate with your project. First, the article underscores cyber sextortion as the initial step in a multi-layered exploitation process. Second, it raises the important issue of "possession" in the context of image-based sexual abuse, where streaming distribution is becoming more prevalent. Third, the article highlights the responsibility of digital platforms to prevent the spread of exploitative content. In the "Nth Room" case, Telegram's refusal to cooperate with the investigation due to privacy concerns is a critical point.
The research also identifies challenges in combating these crimes, such as the limitations of tracing cryptocurrency transactions across foreign exchanges and the ease with which evidence can be deleted on platforms like Telegram. These insights are valuable for your project as you explore the connections between criminal methodologies and the technological features that enable them.
Charles, Angela T. The Abuse of Teenagers by Online Predators Facilitated Through the Internet and Social Media. MS Thesis. Utica College, May 2017. Feb 17 2021, pp. 1-17.
This article provides a valuable framework for analyzing cyber sexual abuse, particularly relevant to the "Nth Room" case. The author effectively introduces key concepts and terminology related to cybercrime, including the distinction between "advanced cybercrime" and "cyber-enabled crime." Critically, the article focuses on cyber-enabled crimes, which encompass sexual extortion and exploitation – the core methods of abuse in the "Nth Room" case. This contextualization helps position your research within the broader landscape of cyber sexual abuse.
Beyond definitions, the article explores the ways in which the internet and social media facilitate these crimes. It delves into various types of online sexual predators and their methods. The chapter "The Different Acts of Abuse that are Committed Using the Internet" is particularly insightful, providing detailed explanations of relevant methods like human sex trafficking (sexual exploitation) and sextortion, both crucial aspects of the "Nth Room" case.
O'Malley, Roberta L. Holt, Karen M. Cyber Sextortion: An Exploratory Analysis of Different Perpetrators Engaging in a Similar Crime. Journal of Interpersonal Violence, 2020, pp. 1-26.
This article, focused on cyber sextortion as a form of image-based sexual abuse (IBSA), provides valuable insights for analyzing my project's subject. The authors, experts in sexual violence and deviance, conducted a qualitative content analysis of media articles and court documents related to 152 cyber sextortion offenders. Their analysis identified four key themes, including two particularly relevant to the "Nth Room" case: minor-focused offenders and cybercrime-oriented offenders.
The article highlights three key characteristics that differentiate cyber sextortion from other interpersonal crimes: the cyberspace element, the possession of compromising material, and the extortion component. Interestingly, the research suggests that despite diverse motivations (sex, power, dominance, coercion, or money), cyber sextortion offenders often employ similar methods. Furthermore, the article's data-driven approach offers valuable examples for structuring my own analysis.
III. PRODUCT




IV. PUBLISHING
National Undergraduate Research Conference on Science, Technology, Medicine and Society
Vassar College | 2021
"The STMS Conference is an opportunity for undergraduates from across divisions to present their research on myriad topics related to the intersections of science, technology, medicine, and society."
Read More
Anthropology & Design Exhibition
The New School | 2021
"ADX invites students from varied disciplinary backgrounds to explore and experiment with anthropological and design research methods that open up new epistemological and creative possibilities, and illuminate our lived experiences and
imaginations. The exhibition consists of a virtual reality showcase and a series of virtual moderated panels with artists and presenters."
Read More
GALLERY 1 (AUTO)ETHNOGRAPHY & MAPPING
VR Exhibition Space